Supply Chain Attacks: When you are attacked by the suppliers you trust the most
Imagine that you have installed the most expensive armored door at the entrance to your company, you have cameras and guards. No one can enter uninvited. But what do you do if the thief is the very plumber you called to fix the sink and to whom you willingly opened the door?
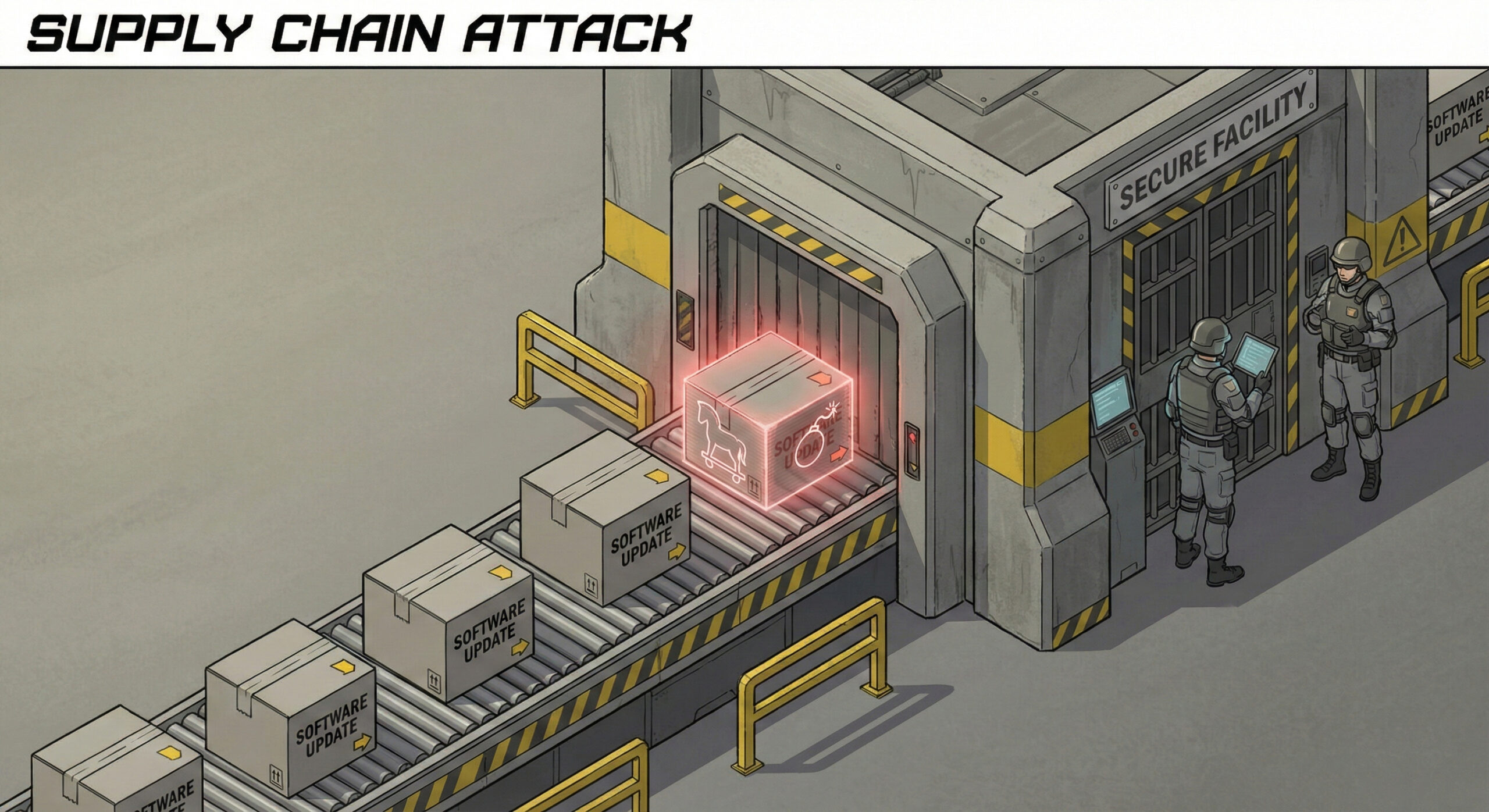
In the digital world, this scenario is called a Supply Chain Attack. In 2026, hackers have understood that large companies are difficult to break directly, so they attack easier targets: their software suppliers. At Altanet Craiova we believe this is one of the most insidious risks for today's business environment.
What does a supply chain attack mean?
Modern companies don't build all their software from scratch. We use dozens of "ready-made" programs: accounting applications, website plugins, printer drivers, or network monitoring platforms.
Hackers don't attack you. They break into the servers of the company that produces that software (the vendor) and infect the next update. You, being a conscientious customer, do your update thinking it's for your own good. In reality, you've just installed the virus yourself into the heart of your system.
Why is it so dangerous?
This type of attack bypasses almost all classic security measures:
- Blind Trust: Your antivirus trusts software digitally signed by large manufacturers (such as Microsoft, Adobe, or local ERP vendors). If the source is compromised, the antivirus will not detect anything suspicious initially.
- Privileged Access: Maintenance or administration programs usually run with maximum privileges (Administrator). Once infected, they give hackers the keys to the entire kingdom.
How do you protect yourself from your own suppliers?
It's difficult, but not impossible. You need to adopt a "Zero Trust" mentality:
- Software Inventory: You need to know exactly what software is running in your company and who makes it. Are you using an obscure WordPress plugin made by a student? That's a weak point.
- Behavior Monitoring: Even if a program is “trustworthy,” if it suddenly starts sending data to a server in Russia or China in the middle of the night, it should be blocked immediately. Endpoint Detection and Response (EDR) tools do exactly that.
- Network segmentation: Don't let the print server communicate with the database server. If the print provider is compromised, hackers will remain isolated there.
To see concrete examples and understand the mechanics behind these incidents, you can read the explanations in the Cloudflare's Learning Center on Supply Chain Attacks.
Conclusion
Your security is only as strong as the weakest link in your supply chain. It's not enough to protect yourself; you must demand high standards from everyone you work with.
Do you want to know if your network is ready to detect suspicious activities coming from the inside? We offer advanced monitoring solutions and proactive IT services. Visit our contact page and let's secure the entire chain.
This material is part of Altanet's educational series on digital security. Want to know what other risks you are exposed to this year? See Complete list of cyber threats in 2026.

Leave a reply